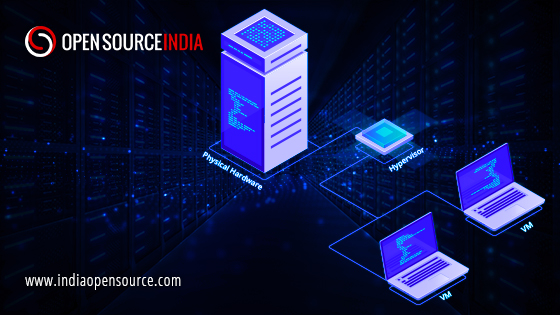
What is Virtualization?
Virtualization employs software to establish an abstraction layer over the computer hardware to divide the hardware components of a single computer—processors, memory, storage, and more—into several virtual computers, also known as virtual machines (VMs).
To simulate hardware functions and build a virtual computer system, virtualization needs virtualization software or Hypervisors. This makes it possible for IT companies to run different operating systems, applications, and virtual systems on a single server. Virtualization benefits the efficient processing of the computer system. Virtualization means establishing an abstract layer between the OS and the applications. It uses hardware, software, and functions as an isolated container on the physical server and operating system.
These containers perform the role of a servers.
Why are Virtual Machines Used?
- New computer environments can be added to existing hardware thanks to virtual machines (VMs). Instead of investing in new hardware resources, this enables firms to make greater use of what they already have.
- VMs does not require physical space. It is a highly crucial factor for large-scale organizations.
- VMs are temporary. If the VM is no longer in use, it can be deleted from the physical server. It is easier faster and more cost-effective to install a new VM than to install a new physical system.
- A VM is easily portable and can be moved from one physical system to another allowing its processes to be performed at different locations.
- A VM is as secure as a separate physical machine without the effort of installing a new Physical machine.
What is a hypervisor?
A hypervisor also called a Virtual Machine Manager (VMM) is a layer between the physical server and the virtual machine. It separates the hardware resources like CPU/processor power, RAM, network bandwidth, etc. from virtual machines and distributes the physical resources to the virtual machines. It is a program that isolates, partitions or abstracts the VMs to run without any interruptions of resource outages.
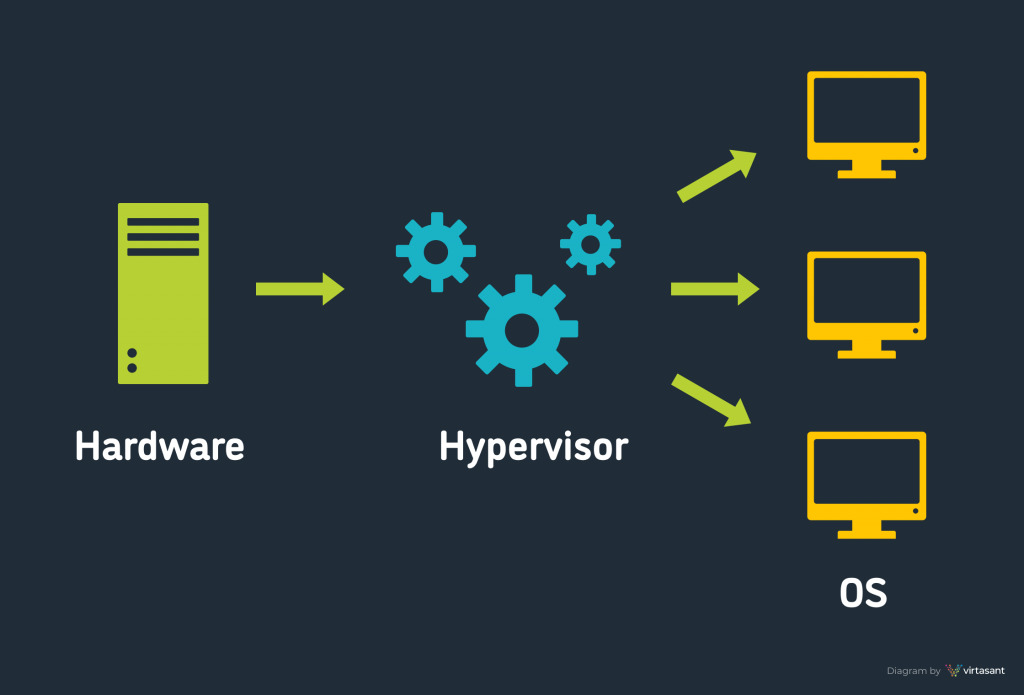
Hypervisors have 3 modules on which they work
- Dispatcher – The dispatcher functions as the monitor’s entry point and diverts the virtual machine instance’s commands to one of the other two modules.
- Allocator – The choice of which system resources to give the virtual machine instance is made by the allocator. The dispatcher calls the allocator whenever a virtual machine tries to execute an instruction that modifies the machine resources connected to the virtual machine.
- Interpreter – There are interpreter procedures in the interpreter module. When a virtual machine performs a privileged instruction, they are carried out.
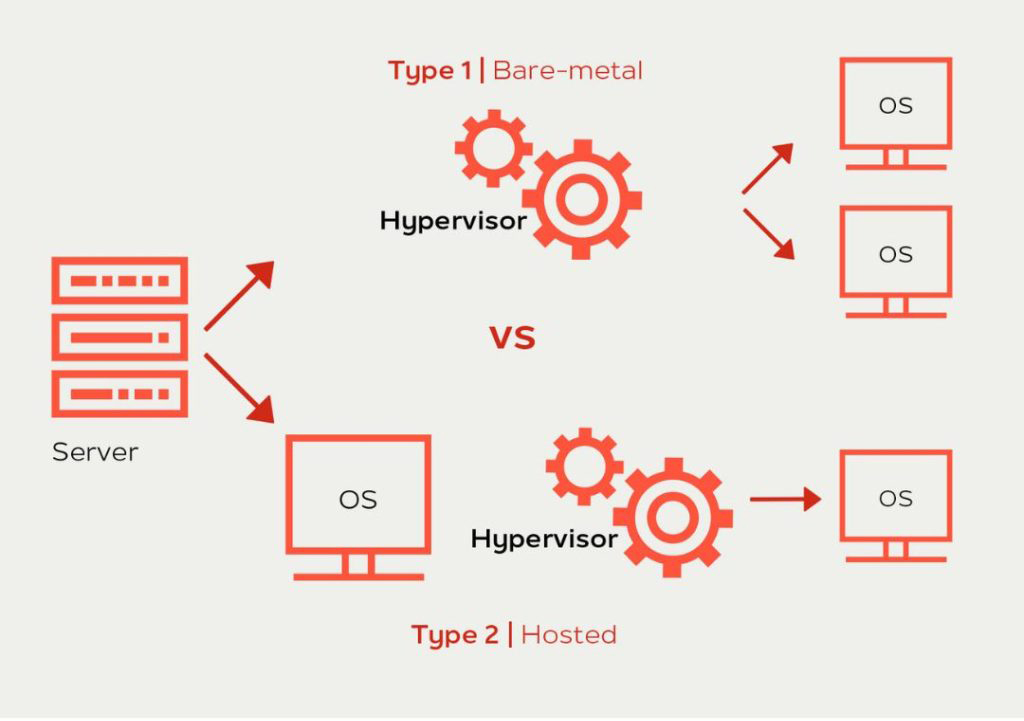
Types of Hypervisor
Type 1 hypervisor
Also known as “Native Hypervisor” or “Bare Metal Hypervisor” , it can directly access the hardware resources as no other layer is available between hardware and hypervisor programs.
Microsoft Hyper-V , Citrix XenServer , and VMware ESXi are a few examples of Type 1 hypervisors.
Because they have immediate access to the physical hardware resources, these hypervisors are incredibly effective (like CPU, Memory, Network, and Physical storage). The security is another advantage of a bare-metal hypervisor as it does not rely on any third-party resource or Operating System. These hypervisors need dedicated physical machines to manage hardware resources and control different virtual machines.
Type 2 hypervisor
Also known as Hosted Hypervisor, it runs on an underlying host system. These hypervisors don’t run directly on a physical server, instead, need a layer of OS to run. The hosted hypervisor is installed on the operating system of the physical machine and asks the operating systems to call for hardware resources. These hypervisors are useful to check malicious codes, malware, etc.
Users can run a virtual machine while running the host machine. The installation is quick and easy.
Having no direct access to the hardware, the hypervisor needs to ask the operating system for a hardware call, the process lags the performance of these hypervisors as compared to the Type 1 hypervisors. Microsoft Virtual PC, Oracle Virtual Box, VMware Workstation, Oracle Solaris Zones, VMware Fusion, Oracle VM Server for x86 are some popular Type 2 hypervisors.
Which Hypervisor should you go for?
A bare-metal hypervisor gives better efficiency while hosted hypervisors are easy to set up. Both hypervisors have their own benefits and limitations but you should go for one according to your needs. It also depends on the size of the company, the criticality of operations, IT infrastructure, the skills of your employees, and the budget for premium features of hypervisors.
A Type 2 hypervisor is a better option for organizations that are just starting with the concept of virtualization only if latency can be ignored. It is easy to set up in the available devices and is flexible with physical systems. For those organizations where, computational power plays a key role in operations, a Type 1 hypervisor is a better choice.
FAQs
-
What is hypervisor in cloud computing ?
A Cloud Hypervisor is software that enables the sharing of cloud provider's physical compute and memory resources across multiple virtual machines (VMs).
-
What is the difference between virtualization and hypervisor?
Its type includes Native hypervisor and Hosted hypervisor. It is used to allocate each VM resources such as CPU, memory, storage, and network to simply run guest OS and applications.
-
What is the main function of hypervisor?
What is the main function of a hypervisor? Hypervisors separate a system's operating system (OS) and resources from the physical machine. They organize these separated resources into files called virtual machines (VMs). Then, they assign computing power, data, and storage to each one.
-
What are two types of virtualization?
When it comes to desktop virtualization, there are two main methods: local and remote. Local and remote desktop virtualization are both possible depending on the business needs. However, local desktop virtualization has many limitations, including the inability to use a mobile device to access the network resources